data recovery agent (DRA)
What is data recovery agent (DRA)?
A data recovery agent (DRA) is a Microsoft Windows user account with the ability to decrypt data that was encrypted by other users. The DRA account allows an IT department to recover data that was encrypted by an employee in the event that the original recovery key or passphrase is lost or if the employee leaves the company. The DRA is used for Microsoft Encrypting File System (EFS), Windows Information Protection (WIP) and BitLocker.
How does a data recovery agent work?
The data recovery agent allows an administrative account to decrypt and read any EFS encrypted file in an organization. The DRA account is provisioned with an X.509 certificate. A second protector is added to every EFS file at encryption that the DRA certificate can unlock. This makes the DRA and its certificate extremely sensitive. It should be protected and only used when needed. It is not recommended to have the DRA be a normal account or one in regular use by administrators.
Each EFS encrypted file has a unique File Encryption Key (FEK), which is also protected by encryption. With an assigned DRA, two separate copies of the FEK are made: one is encrypted by the user public certificate, and the other is encrypted by the DRA public certificate. Both encrypted FEKs are stored with the encrypted file. This allows both the user and DRA to decrypt the file without the other, and the DRA can recover the file even if the user encrypting certificate is lost.
An administrator can also revoke user access to the encrypted file, while maintaining access by the DRA. This reduces the amount of information that is saved because only one recovery certificate needs to be stored that can access every file.
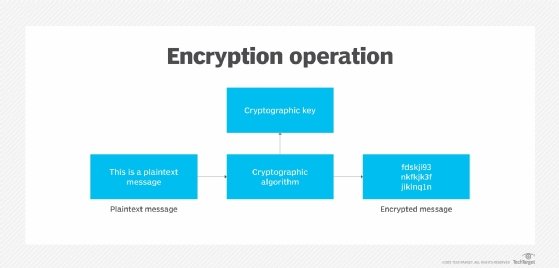
To illustrate how a DRA works, imagine an office building with many offices and key locks on the doors. Each worker (user) needs to be able to unlock their office door, and for the sake of this illustration they may have more than one office. At the same time, maintenance personnel (DRA) also need to be able to unlock every door. In this scenario, each employee would need a key for the one or more doors they need to unlock, and maintenance personnel would need a copy of every key. This would result in the number of keys in use quickly getting out of control.
A solution to this problem is to have two copies of the key that unlock the door (FEK) installed in a lock box next to the door they unlock. Both the employee and maintenance person can use their key to unlock the lock box. This way each person only needs one key to open any door they have access to. To update access only the key boxes need to be changed.
The DRA must be set before any files are encrypted. This is because the DRA key is added at encryption. Any files encrypted before the DRA is added cannot be unencrypted by the DRA.
Where are data recovery agents used?
DRAs are used in Microsoft Encrypted File System (EFS), which has been a part of all Windows versions since Windows 2000, including Windows Server, Windows 7, Windows 10 and Windows 11. In Windows 2000 the local administrator account is the DRA. In all later editions there is no default DRA, and it must be set through policy.
WIP, previously called enterprise data protection, is a technology to protect against data leaks by encrypting corporate data. WIP relies on EFS as the underlying technology to handle file level encryption. WIP uses a DRA to provide administrator access to all protected files.
Microsoft BitLocker is a full disk encryption (FDE) technology. It is not EFS based and does not have assigned DRAs, but it does use a similar "recovery agent." A BitLocker recovery agent can unlock any organization BitLocker protected disk. This is useful for organizations that require FDE on all removable media, such as USB thumb drives, because it allows an administrator to recover a drive if the password is lost.
How to set the disaster recovery agent
The DRA is designed to be used in an organization. It is set in a Microsoft Windows policy framework, such as Microsoft Active Directory Group Policy, Microsoft Endpoint Configuration Manager, mobile device management (MDM) or Microsoft Intune.
The first step when creating a DRA is to generate a data recovery agent key (DRA key). This is a certificate with a public/private key pair that will act as the recovery key. It can be generated with the built-in Windows executable cipher. [Run the command "cipher /r:FILENAME" to generate a .cer and .pfx file.] Alternatively, the certificate can be generated from a public key infrastructure (PKI).
To deploy a DRA using Microsoft Active Directory Group Policy, the user must open the Group Policy Object Editor, then navigate to Configuration\Windows Settings\Security Settings\Public Key Policies\Encrypting File System, right-click on Encrypting File System in the right-hand pane and select Create Data Recovery Agent. This will open a wizard to add the DRA to the domain using the pregenerated certificate or by adding a user account with a published certificate from Active Directory.
To deploy a DRA for WIP using Microsoft Endpoint Configuration Manager, the user creates a configuration item in the configuration item's node of Microsoft System Center Configuration Manager (SCCM), and for the device settings to configure select Windows Information Protection. Then, the wizard is used to create the WIP policy. In the setup wizard, one step is required to "Upload a Data Recovery Agent (DRA) certificate to allow recovery of encrypted data" where the user can browse to select the DRA certificate that was created.
To deploy a DRA for WIP using Microsoft Intune, the user creates a WIP policy. This is done in Intune under Apps > App protection policies > Create policy. The wizard is used to create the WIP policy, by clicking the Advanced settings button in the policy setting section. There is an option to "Upload a Data Recovery Agent (DRA) certificate to allow recovery of encrypted data" where the user can browse to select the DRA certificate that was created.
See also: Comparing data protection vs. data security vs. data privacy and 3 areas privacy and cybersecurity teams should collaborate.







