The complete guide to ransomware
Organizations in every industry can be targets of cybercrime for profit. Get expert advice on ransomware prevention, detection and recovery in our comprehensive guide.
When it comes to security challenges, businesses of all sizes are alarmed by the abundance and gravity of ransomware attacks. Cybercriminals have targeted every industry with specialized malware, collecting untold amounts in ransom. This comprehensive guide on ransomware explains the types of attacks, common attack vectors, prevention methods and tools, and best practices for recovery.
What is ransomware?
Ransomware is a subset of malware that can lock and encrypt data on a victim's computer. Attackers then notify the victim that an exploit has occurred and the data will not be unlocked or decrypted until a payment is received.
To be clear, malware is the umbrella term for any malicious code or program that gives an attacker explicit control over a system. Ransomware is specific to when attackers demand payment to unblock access or unencrypt the data and allow victims to regain access. Often, ransomware results in the crime of cyberextortion. If attackers exfiltrate a victim's data and then threaten to leak it if their demands aren't met, the malicious code that started the attack is referred to as extortionware.
Types of ransomware
Ransomware has multiple types that malicious actors use to extort ransoms. The traditional types are crypto and locker. Two newer types -- double extortion and ransomware as a service -- have been gaining popularity among malicious actors.
- Locker blocks access to computers, and attackers require payment to unlock access.
- Crypto encrypts all or some files on a computer, and attackers require payment before handing over a decryption key.
- Double extortion occurs when cybercriminals demand one payment to decrypt the files and another not to make them public.
- Ransomware as a service (RaaS) occurs when cybercriminals can access malicious code for a fee.
Ransomware is often known by its malware strain code names, such as AIDS Trojan, which first appeared 30 years ago. Since then, names such as GPcode, Achievus, Trojan WinLock, Reveton and CryptoLocker have made headlines for the havoc they caused. In the past decade, LockerPIN, Ransom32, WannaCry, Goldeneye and Petya emerged. And recently, a cybercrime gang used the RaaS variant, REvil, to demand $70 million in ransom from software technology company Kaseya.
Read our detailed history of ransomware strains.
Ransomware vectors
Ransomware infiltrates organizations through three common vectors: phishing, Remote Desktop Protocol (RDP) and credential abuse and exploitable vulnerabilities.
Phishing
Phishing, which targets an organization by embedding malware in email, remains one of the most popular ways for cybercriminals to deliver their payload. Phishing emails have become much more sophisticated, enticing even the savviest of users to click on damaging links.
RDP and credential abuse
Cybercriminals can inject malware through RDP, which is Microsoft's proprietary protocol for secure remote access to servers and desktops. When an RDP environment is left unsecured, attackers gain access through brute force, legitimate credentials purchased through criminal sites and credential stuffing.
Vulnerabilities from poor patching practices
Attackers look for vulnerabilities they can exploit, and unpatched systems are an attractive entryway. Websites, including plugins, and complex software environments that link to third parties enable malware to be inserted undetected.
Dig deeper into how malware can be distributed through vulnerabilities in websites and browsers.
Top ransomware targets
While it seems that no industry is spared from ransomware, some are more susceptible to it than others. For instance, educational institutions have suffered greatly at the hands of attackers. TechTarget Senior Writer Alissa Irei relayed one Washington school system's reaction and the top 10 ransomware targets by industry:
- education
- retail
- business, professional and legal services
- central government (including federal and international)
- IT
- manufacturing
- energy and utilities infrastructure
- healthcare
- local government
- financial services
As Irei noted in the article, the size of the organization is not always the determining factor; instead, it is where attackers can extract the maximum financial impact.
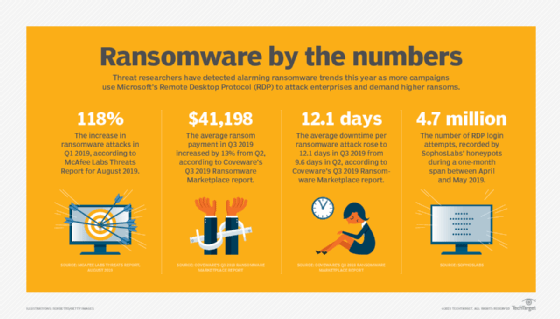
Some of the most notable ransomware attacks include the following recent victims:
- An attack on Colonial Pipeline led to a multiday disruption of the fuel supply for a large swath of the East Coast. Colonial paid a $4.4 million demand to speed its recovery efforts. Some of that payment, made in cryptocurrency, was later recovered by the U.S. government.
- Global beef manufacturer JBS USA had to shutter operations for several days after it was hit by a ransomware attack. The company paid attackers $11 million to ensure no data was exfiltrated.
- The Buffalo Public Schools system in New York ceased instruction -- in-person and online -- in the wake of a crippling ransomware attack. The system required a week to get back on its feet and resume classes.

How to recognize attacks
Ransomware attacks are uniquely difficult to detect as the malicious code is often hidden in legitimate software, such as PowerShell scripts, VBScript, Mimikatz and PsExec. Organizations must use a combination of automated security tools and malware analysis to uncover suspicious activity that could result in a ransomware attack.
Here are three types of ransomware detection techniques:
- signature-based ransomware compares a sample hash gathered from suspicious activity to known signatures;
- behavior-based ransomware examines new behaviors in relation to historical data; and
- deception uses a lure such as a honeypot that normal users wouldn't touch to catch attackers.
Ransomware attacks happen quickly, and it is important to be able to detect and respond just as quickly. Read about three ransomware incidents and their outcomes.
How to prevent ransomware attacks
Organizations can lessen their vulnerability to ransomware attacks and limit the damage they cause by assuming a strong cybersecurity posture. Mike Chapple, senior director of IT with the University of Notre Dame, outlined the following steps to prevent ransomware attacks:
- Maintain a defense-in-depth security program.
- Consider advanced protection technologies -- such as zero trust and endpoint detection and response.
- Educate employees about the risks of social engineering.
- Patch regularly.
- Perform frequent backups of critical data.
- Don't depend solely on backups.
In addition, enterprises can implement business processes that limit or even eliminate transactions via email to make links and attachments stand out more and become more suspicious to security professionals.
The cloud offers a unique specter of ransomware protection, as organizations can use it for a backup and recovery strategy. Companies can create isolated backups that can't be accessed from the core corporate environment without making infrastructure changes or requiring numerous administrative authentication/authorization adjustments, according to Dave Shackleford, founder and principal consultant at Voodoo Security.
How to respond to and recover from ransomware attacks
Once a ransomware attack happens, organizations must follow the ransomware incident response plan that they ideally would have created and tested well ahead of the attack.

Organizations will want to try to remove the ransomware, but that can be incredibly challenging. Security professionals must make sure they don't allow the malware to penetrate further into the system. The following steps for ransomware removal from independent IT consultant Paul Kirvan will help:
- Isolate the infected device.
- Determine the ransomware type to enable more targeted remediation efforts.
- Remove the ransomware, which can involve checking if it is deleted, using antimalware or anti-ransomware software to quarantine it, asking external security professionals for help, and if need be, removing it manually.
- Recover the system by restoring a previous version of the OS before the attack occurred.
Ransomware detection and removal tools can help automate or at least speed up recovery times. They can delete all malware on a device to ensure it is clean. Kirvan highlighted 17 ransomware removal tools that can detect threats, block attacks and erase lingering traces of malware.
Negotiating ransomware payments
Determining whether to pay a ransom in the middle of a ransomware attack can be harrowing. Companies should already know their criteria for complying or not complying with demands. They should know if they can trust their ability to quickly recover systems and backups if they deny attackers. And they should know what vulnerabilities they have in the data that attackers have locked, encrypted and potentially exfiltrated.
Some common reasons to pay ransoms include the following:
- faster recovery time;
- damage to business;
- excessive recovery costs; and
- protection of customer or employee data.
Companies might decide not to hand over a ransom because they believe it might encourage other attackers or could escalate future payments. Additionally, there is no guarantee the data will be returned, and paying the ransom could subject the company to legal issues.
If companies are unsure about whether to acquiesce to attackers, they can tap into the skills of an expert negotiator. Negotiators also can be used to interact with threat actors and help settle on a ransom amount. These services are sometimes addressed in cyber insurance contracts.
Not surprisingly, cyber insurance coverage has changed considerably with the rise of ransomware, and organizations should review policies carefully to ensure ransomware attacks are covered.
Companies will want to be covered for the following:
- business and dependent business (a cloud provider or software vendor) interruption;
- data recovery; and
- security incident and breach costs.
Organizations will likely need to report any ransomware attack as well.
Ransomware attacks are increasing, so companies need to understand their risks and coverage, and be prepared to address attacker demands accordingly.
Latest ransomware news and trends
Verizon 2023 DBIR: Ransomware remains steady but complicated
Chris Novak, managing director of cybersecurity consulting at Verizon Business, said 2023 was a "retooling year" for ransomware threat actors adapted to improved defenses.
Users dish on ransomware protection, recovery at VeeamON
To help protect against and recover from ransomware attacks, IT professionals at VeeamON 2023 recommended planning, testing and other key security measures.
Biggest healthcare data breaches reported this year, so far
The biggest healthcare data breaches reported this year so far have impacted more than 39 million individuals collectively.
Clop begins naming alleged MOVEit victims
Clop uploaded details of 12 new victims to its dark web leak site in June, many of them likely linked to the ongoing MOVEit cyber attack.
May ransomware activity rises behind 8base, LockBit gangs
NCC Group's May threat intelligence report revealed that a new ransomware gang named 8base was a key contributor to the month's high number of victims.
Ransomware takes down multiple municipalities in May
City and local governments experienced severe disruptions to public services due to ransomware attacks in May, particularly from the Royal ransomware group.






