
Alex - stock.adobe.com
What are the Microsoft 365 password requirements?
When IT administrators manage passwords for Microsoft 365 accounts in Azure AD, they can deploy and remove critical policies that can improve overall security posture.
When it comes to Microsoft 365 security, one of Microsoft's top best practices is to enable multifactor authentication.
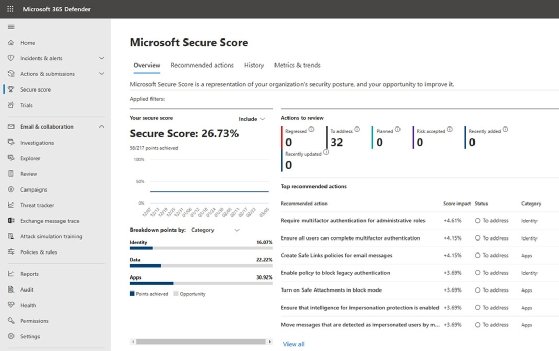
In fact, the very first item on the Microsoft Secure Score list of recommended actions is to require multifactor authentication (MFA) for administrator accounts (Figure 1). Regardless, MFA is only one piece of the overall security puzzle and admins also need to revisit their Microsoft 365 password policy to make sure that it is in line with their organization's security requirements.
Given the importance that Microsoft places on MFA, it may be tempting to think of password policies as relatively unimportant. Even so, protecting users' passwords remains a critical task.
Consider why organizations use MFA in the first place. The idea is that if a user's password was to become compromised, then the stolen password alone will not be sufficient to gain access to the user's account.
To put it another way, when administrators enable MFA, they are essentially requiring users to provide two pieces of information at login instead of just one.
With that in mind, suppose for a moment that an organization were to adopt MFA because it considers MFA superior to standalone passwords. In this case, perhaps the organization would begin to regard its password policy as relatively unimportant. Assume that the organization began placing almost no length or complexity requirements on their users' passwords.
In such a situation, the organization in question is virtually guaranteeing that the users' passwords will eventually become compromised as the users rely on passwords that are far less secure. Even though there are methods that cybercriminals can use to beat MFA challenges, let's pretend for a moment that the organization's MFA policy is effective at preventing cybercriminals from logging in using MFA.
The reason why MFA is so effective is because it requires anyone who is logging in to provide two pieces of information instead of just one. If an organization adopts weak password policies, then it is effectively surrendering its users' passwords to cybercriminals. This means that a cybercriminal now needs that single other piece of information in order to log into the network. In other words, using MFA without also using strong password policies effectively undermines MFA's main benefit.
The Microsoft 365 password policy
Microsoft 365 is built on top of Azure Active Directory (Azure AD), which means that Microsoft 365 users are really just Azure AD users who have been licensed to run Microsoft 365. Microsoft automatically applies a basic password policy to Azure AD users. Some of the items in this password policy can be changed while others cannot.
The main aspect of the Azure AD password policy that administrators cannot change is the length and complexity requirements. Passwords must be at least eight characters long and be made up of three out of these four items: lowercase letters, uppercase letters, numbers and symbols.
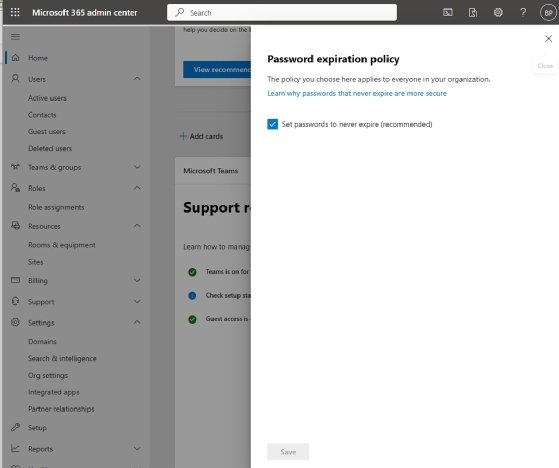
Although Microsoft no longer recommends that organizations force periodic password expirations, Azure AD's default behavior is to expire passwords every 90 days. To change this behavior, open the Microsoft 365 Admin Center and type the word "password" into the search box. The search results will provide a link to the password expiration policy. Clicking this link takes the admin to a screen where they can configure passwords to never expire (Figure 2).
Customizing MFA and password controls in Azure AD
Although not technically part of the password policy, Azure AD's password protection feature is a way to further enhance and strengthen password security. To access this tool, open the Azure AD Admin Center -- also known as the Microsoft Entra Admin Center. When the console opens, enter "password" into the search box and then click on the Azure AD Password Protection link.
The Password Protection screen offers several different settings that admins can use to enhance their password security (Figure 3). For example, an administrator can set the lockout threshold and lockout duration for managed accounts. Likewise, admins can create a custom list of banned passwords. For example, it may be a good idea to ban the use of the company's name as a part of a password.

How to deploy password controls to on-premises Active Directory
If an organization has strict requirements for its password policy, then it's entirely possible that Microsoft's password controls in Azure AD will be inadequate. However, there is another way to gain greater control over your password policies.
The important thing to keep in mind is that the Azure AD password policies only apply to cloud-native accounts. They do not apply to on-premises accounts or accounts that have been synchronized from an on-premises environment. That being the case, those who need greater control over their password policies can set up an on-premises Active Directory environment and use Azure AD Connect to synchronize the on-premises environment to Azure Active Directory. This will allow admins to set password policies at the Active Directory level and have those password policies apply to the Microsoft 365 environment so long as the Microsoft 365 users are being synchronized and are not cloud only.








